app development
security
+ 4 more ...
Cybersecurity: Why it matters
11 Feb 2020
by Lotte, Digital Content Specialist
11 Feb 2020
by Lotte, Digital Content Specialist
app development
security
privacy
cybersecurity
cloud storage
encryption
Cybersecurity: Why it matters
Table of contents
Contact us
We will get back to you in the next 48 hours.

The more information we put on the internet, the more we must rely on cybersecurity and data privacy.
January 28th is World Data Privacy Day, and although it’s great to have one day a year to raise awareness about data privacy, it is something we should be aware of every day. The internet is a great place to connect ourselves to the rest of the world, but it also brings along quite some bad stuff. The amount of sensitive information we put online is skyrocketing, and no one wants their data to fall into the wrong hands. This is why cybersecurity is key, but what exactly is this mysterious force that keeps our information safe? Let us explain.
What is cybersecurity?
It’s all in the name: cybersecurity entails everything that has anything to do with the protection of the information we put online every day. Especially in a time where, for example, social media platforms require more and more of our personal information, from our date of birth to email addresses and phone numbers, it’s essential that this data stays on that specific platform.
Next to that comes the fact that, with the ever-growing world wide access to the internet, there’s an increasing amount of people that might use the internet with bad intentions. Whereas twenty years ago, hackers mostly happened to be young tech-savvy people with too much time on their hands, the current hacker community consists of entire criminal organizations, aiming their attacks on governmental agencies and leading financial institutions. Most of these institutions, from the US government to Google or Apple, have their own team of professional hackers to prevent them from being attacked by outsiders. Did you know that, as of 2020, there’s a hacker attack every 39 seconds? That fact alone is reason enough for crucial alertness on cybersecurity.
Data handling on social media platforms
We’re already aware of the fact that most social media platforms have the right to share our personal information with third parties for, for example, personalized advertisements. (In case you weren’t aware of that, we would recommend you take some time to look into it) After all, we can use platforms like Facebook and Instagram for free, because we practically “pay” with our personal information. Luckily, we can somewhat decide what data Facebook is allowed to sell to third parties, but we have very little influence on what exactly happens to that data in general.

Social media platforms like Facebook, Instagram, and Twitter all have a very extensive statement on how they handle user data and handle privacy. It’s all in the terms and conditions, which everyone surely reads before creating an account, right? The fact that these statements are consciously hidden in often hazy and content-packed documents, has the result that very few of us actually take the time to read it. This causes users to be unaware of what happens to their personal information. Yet, many platform users actually don’t seem to care about it that much. “I have nothing to hide, why would I worry?” Or “Facebook only sells it to third parties. They still prevent my data from becoming publicly available.”
These are often used reasons for people not to worry about the handling of their data, but in reality, there’s no guarantee our information actually stays protected once it arrives in the hands of these third party advertisers. As a user of social media platforms it is your choice to decide if you’re okay with paying with your data, or not use the platform at all. Although we don’t have much control on what happens to our data on social media platforms, it’s already a first step to spread awareness about it.
Instant-messaging apps and encryption protocols
Since the rise of instant-messaging applications like WhatsApp, most of our communication happens within online spheres. We never questioned the safety of our messages, and the fact that there, just like social media platforms, are still third parties with access to these messages. When Facebook took over WhatsApp in 2014, it became clear that there are many ways to intercept the content of our messages. Basically, the entire road between sender and receiver resembles something like a sushi bar conveyor belt, where anyone with access can pick a dish, or in this case, data of their choice. This is where encryption protocols came into sight, and instant-messaging apps like Telegram and Signal gained in popularity.
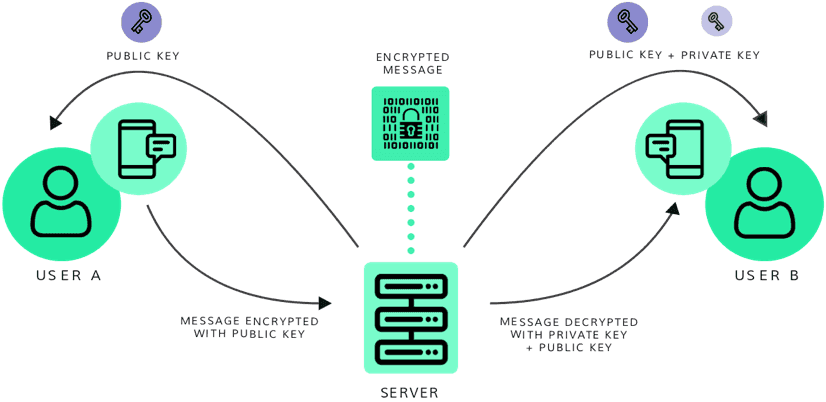
An end-to-end encryption turns your message into a random order of unreadable signs and signals the moment you hit send, and transforms back into the original message with the help of a so-called ‘encryption key’ the moment it arrives at the designated receiver. This way, there should be no chance for external parties to access the contents of your messages. The use of encryption protocols in instant-messaging applications is still a sensitive topic, as it prevents high-level governmental interference, and therefore loses a significant tool for gaining insight in terrorist communication networks. And although we’d expect the government to protect us against the threat of terrorism, most of us still wouldn’t like them to dig through our private conversations. After Edward Snowden revealed insights in governmental interference of private data of citizens in 2013, a worldwide debate was triggered regarding the necessity of data-protection laws. At this moment, there are more than 100 countries with implemented data protection laws, which ensure the protection of private data against unlawful access.
Cloud storage and safe-keeping
An increasing amount of data is being stored in a mysterious database we call the “Cloud”. Think of online services like Google Drive, the Apple iCloud, and Dropbox, in which we store our private pictures and videos, but also confidential documents from our job, or a copy of our passport or credit card. None of these are supposed to end up in the hands of the wrong person, so a solid protection is essential. Just like with instant-messaging applications, data inside a Cloud is often protected by encryption that turns files into a mess of meaningless signs. However, most Cloud services provide encryption while keeping the key for themselves. This means that the service itself can still look into your files. And although that doesn’t seem like a big issue, there’s always a risk of that Cloud service being hacked. In that case, your files are pretty much open to the public, confidential or not. It might be a good idea to check the legitimacy of the Cloud service you are using. If you want to make sure your data is safe, take some time to look into the privacy statements of different Cloud services. And in case you want to be 100% sure about the protection of your data, you can always choose to encrypt your files manually before you upload them in your Cloud.
Cybersecurity at Lizard Global
At Lizard Global we put the privacy of our clients and the safety of your files on a number one priority. This counts for both online storage, but also for software that requires registration for its users. Because of this, our developers make sure all software is created with a guaranteed privacy-by-design. Our skilled team of designers and developers are always up-to-date with the latest changes and innovations in software security. Your information is safe with us, at all times.

The more information we put on the internet, the more we must rely on cybersecurity and data privacy.
January 28th is World Data Privacy Day, and although it’s great to have one day a year to raise awareness about data privacy, it is something we should be aware of every day. The internet is a great place to connect ourselves to the rest of the world, but it also brings along quite some bad stuff. The amount of sensitive information we put online is skyrocketing, and no one wants their data to fall into the wrong hands. This is why cybersecurity is key, but what exactly is this mysterious force that keeps our information safe? Let us explain.
What is cybersecurity?
It’s all in the name: cybersecurity entails everything that has anything to do with the protection of the information we put online every day. Especially in a time where, for example, social media platforms require more and more of our personal information, from our date of birth to email addresses and phone numbers, it’s essential that this data stays on that specific platform.
Next to that comes the fact that, with the ever-growing world wide access to the internet, there’s an increasing amount of people that might use the internet with bad intentions. Whereas twenty years ago, hackers mostly happened to be young tech-savvy people with too much time on their hands, the current hacker community consists of entire criminal organizations, aiming their attacks on governmental agencies and leading financial institutions. Most of these institutions, from the US government to Google or Apple, have their own team of professional hackers to prevent them from being attacked by outsiders. Did you know that, as of 2020, there’s a hacker attack every 39 seconds? That fact alone is reason enough for crucial alertness on cybersecurity.
Data handling on social media platforms
We’re already aware of the fact that most social media platforms have the right to share our personal information with third parties for, for example, personalized advertisements. (In case you weren’t aware of that, we would recommend you take some time to look into it) After all, we can use platforms like Facebook and Instagram for free, because we practically “pay” with our personal information. Luckily, we can somewhat decide what data Facebook is allowed to sell to third parties, but we have very little influence on what exactly happens to that data in general.

Social media platforms like Facebook, Instagram, and Twitter all have a very extensive statement on how they handle user data and handle privacy. It’s all in the terms and conditions, which everyone surely reads before creating an account, right? The fact that these statements are consciously hidden in often hazy and content-packed documents, has the result that very few of us actually take the time to read it. This causes users to be unaware of what happens to their personal information. Yet, many platform users actually don’t seem to care about it that much. “I have nothing to hide, why would I worry?” Or “Facebook only sells it to third parties. They still prevent my data from becoming publicly available.”
These are often used reasons for people not to worry about the handling of their data, but in reality, there’s no guarantee our information actually stays protected once it arrives in the hands of these third party advertisers. As a user of social media platforms it is your choice to decide if you’re okay with paying with your data, or not use the platform at all. Although we don’t have much control on what happens to our data on social media platforms, it’s already a first step to spread awareness about it.
Instant-messaging apps and encryption protocols
Since the rise of instant-messaging applications like WhatsApp, most of our communication happens within online spheres. We never questioned the safety of our messages, and the fact that there, just like social media platforms, are still third parties with access to these messages. When Facebook took over WhatsApp in 2014, it became clear that there are many ways to intercept the content of our messages. Basically, the entire road between sender and receiver resembles something like a sushi bar conveyor belt, where anyone with access can pick a dish, or in this case, data of their choice. This is where encryption protocols came into sight, and instant-messaging apps like Telegram and Signal gained in popularity.
An end-to-end encryption turns your message into a random order of unreadable signs and signals the moment you hit send, and transforms back into the original message with the help of a so-called ‘encryption key’ the moment it arrives at the designated receiver. This way, there should be no chance for external parties to access the contents of your messages. The use of encryption protocols in instant-messaging applications is still a sensitive topic, as it prevents high-level governmental interference, and therefore loses a significant tool for gaining insight in terrorist communication networks. And although we’d expect the government to protect us against the threat of terrorism, most of us still wouldn’t like them to dig through our private conversations. After Edward Snowden revealed insights in governmental interference of private data of citizens in 2013, a worldwide debate was triggered regarding the necessity of data-protection laws. At this moment, there are more than 100 countries with implemented data protection laws, which ensure the protection of private data against unlawful access.

Cloud storage and safe-keeping
An increasing amount of data is being stored in a mysterious database we call the “Cloud”. Think of online services like Google Drive, the Apple iCloud, and Dropbox, in which we store our private pictures and videos, but also confidential documents from our job, or a copy of our passport or credit card. None of these are supposed to end up in the hands of the wrong person, so a solid protection is essential. Just like with instant-messaging applications, data inside a Cloud is often protected by encryption that turns files into a mess of meaningless signs. However, most Cloud services provide encryption while keeping the key for themselves. This means that the service itself can still look into your files. And although that doesn’t seem like a big issue, there’s always a risk of that Cloud service being hacked. In that case, your files are pretty much open to the public, confidential or not. It might be a good idea to check the legitimacy of the Cloud service you are using. If you want to make sure your data is safe, take some time to look into the privacy statements of different Cloud services. And in case you want to be 100% sure about the protection of your data, you can always choose to encrypt your files manually before you upload them in your Cloud.
Cybersecurity at Lizard Global
At Lizard Global we put the privacy of our clients and the safety of your files on a number one priority. This counts for both online storage, but also for software that requires registration for its users. Because of this, our developers make sure all software is created with a guaranteed privacy-by-design. Our skilled team of designers and developers are always up-to-date with the latest changes and innovations in software security. Your information is safe with us, at all times.







