Software Development
Digital Transformation
+ 3 more ...
5 Game-Changing Advancements in Application Security

08 Jul 2025
by Nadiy, Senior Content Writer

08 Jul 2025
by Nadiy, Senior Content Writer
Software Development
Digital Transformation
Cyber Security
Mobile App Development
Web App Development
5 Game-Changing Advancements in Application Security
Table of contents
Contact us
We will get back to you in the next 48 hours.
5 Game-Changing Advancements in Application Security
Application security has evolved far beyond passwords and firewalls. From AI-powered threat detection to quantum-safe encryption, explore the modern strategies that top companies use to stay ahead of evolving cyber threats.
key takeaways
Remember the days when application security was just about strong passwords and firewalls? Seeing that today’s cyberthreats have become more complex, the ways we secure our digital products have had to evolve. The rise of microservices, APIs, remote development teams, and global regulatory standards has created a new playing field—one that demands smarter, faster, and more integrated solutions.
We’re breaking down the five transformative advancements that have fundamentally reshaped how we protect modern applications. From AI-powered threat detection to quantum-resistant encryption, these innovations are not just upgrades—they’re essential for building resilient, future-ready digital systems.
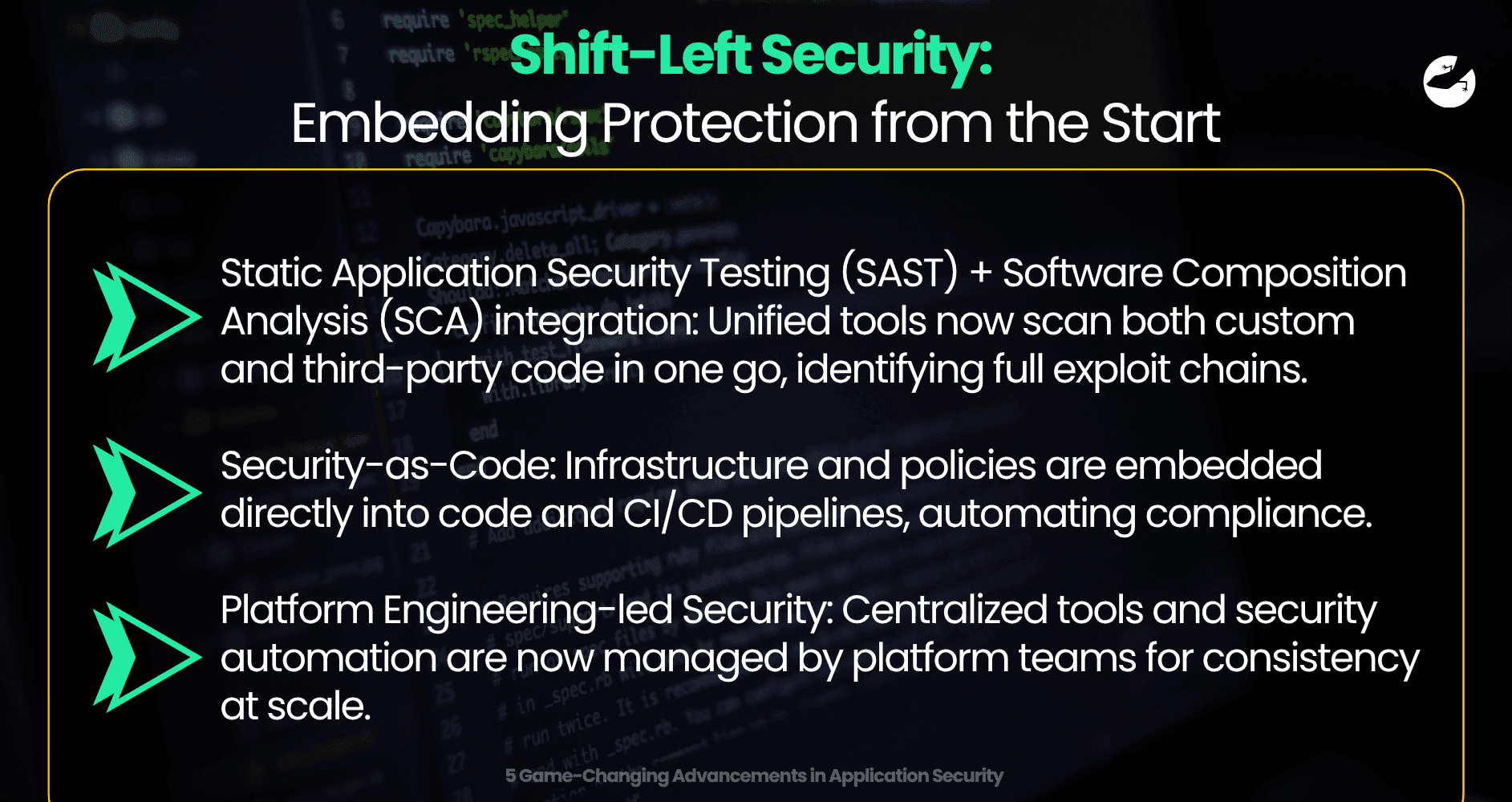
1. Shift-Left Security: Embedding Protection from the Start
Gone are the days when security was treated as a final checkpoint before release. In development cycles today, vulnerabilities introduced early can snowball into massive liabilities. That’s why modern application security starts with the code itself—a practice known as "shifting left."
What’s Changed:
- Static Application Security Testing (SAST) + Software Composition Analysis (SCA) integration: Unified tools now scan both custom and third-party code in one go, identifying full exploit chains.
- Security-as-Code: Infrastructure and policies are embedded directly into code and CI/CD pipelines, automating compliance.
- Platform Engineering-led Security: Centralized tools and security automation are now managed by platform teams for consistency at scale.
By catching and resolving vulnerabilities earlier, organizations reduce risk, save time and money, and ensure developers are actively contributing to a more secure product. This culture shift is the foundation of proactive, scalable application security.
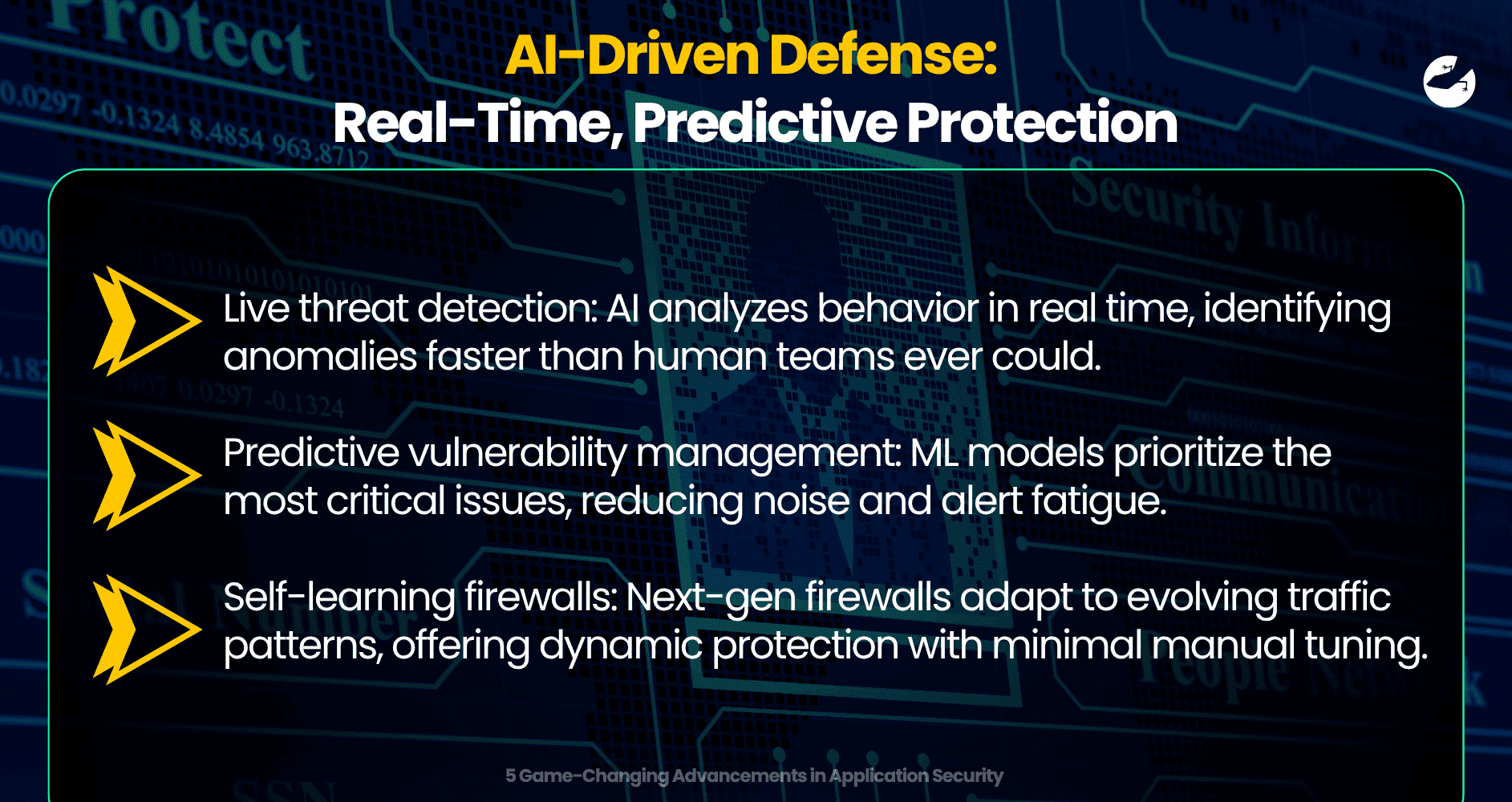
2. AI-Driven Defense: Real-Time, Predictive Protection
As cyberattacks become more sophisticated, reactive security methods struggle to keep up. Artificial Intelligence and Machine Learning have emerged as crucial allies in defending applications, offering speed, accuracy, and predictive power that manual monitoring simply can’t match.
What’s Changed:
- Live threat detection: AI analyzes behavior in real time, identifying anomalies faster than human teams ever could.
- Predictive vulnerability management: ML models prioritize the most critical issues, reducing noise and alert fatigue.
- Self-learning firewalls: Next-gen firewalls adapt to evolving traffic patterns, offering dynamic protection with minimal manual tuning.
These tools don’t just help security teams respond—they help prevent attacks before they happen. AI is enabling a shift from reactive firefighting to proactive defense, making it a game-changer for application security teams.
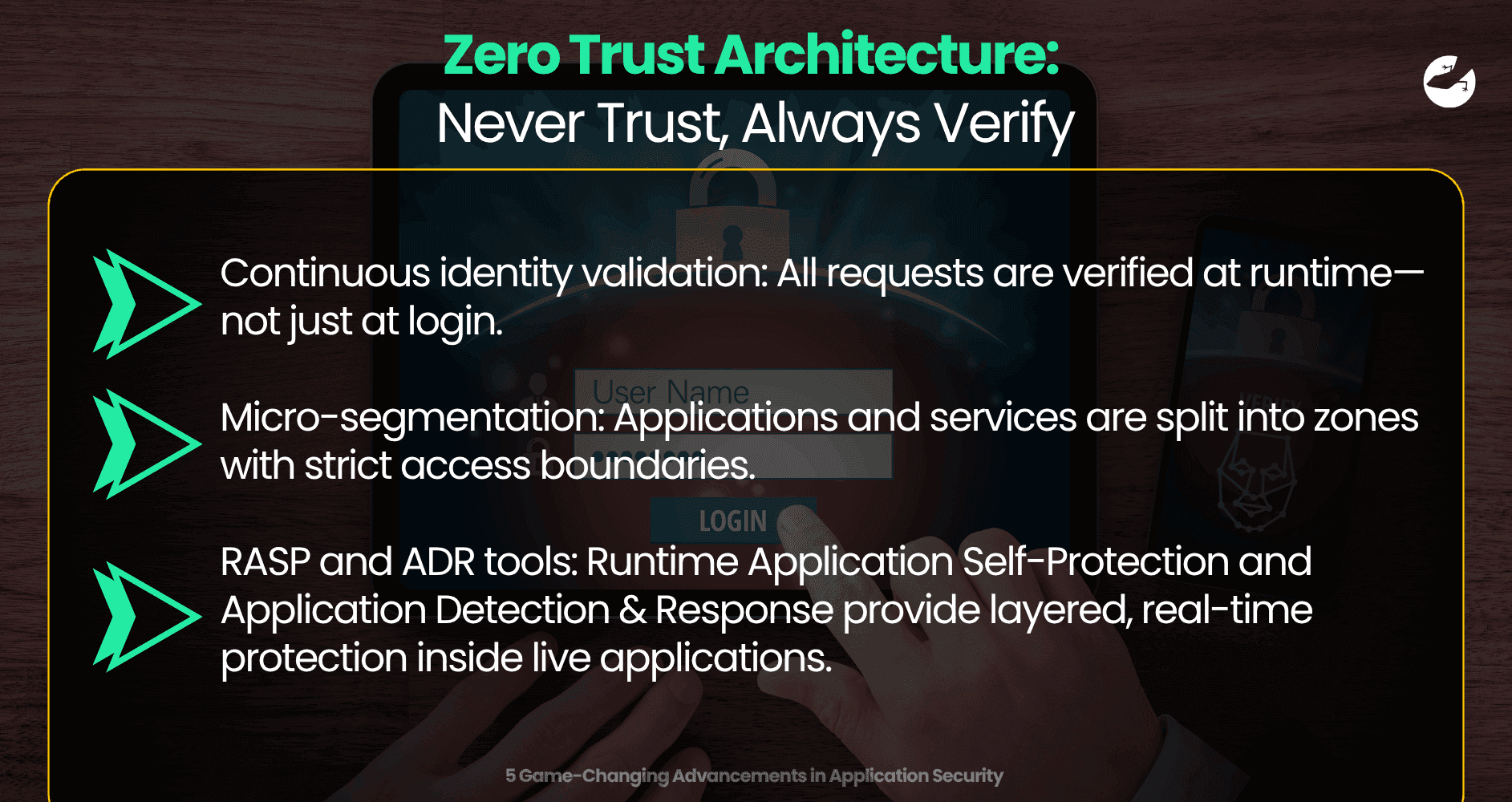
3. Zero Trust Architecture: Never Trust, Always Verify
As applications migrate to the cloud
and users connect from everywhere, perimeter-based security is no longer enough. The Zero Trust model assumes that no entity—internal or external—should be automatically trusted. Every interaction must be verified, authenticated, and authorized.
What’s Changed:
- Continuous identity validation: All requests are verified at runtime—not just at login.
- Micro-segmentation: Applications and services are split into zones with strict access boundaries.
- RASP and ADR tools: Runtime Application Self-Protection and Application Detection & Response provide layered, real-time protection inside live applications.
Zero Trust not only prevents breaches from escalating, it ensures tighter controls over how users and services interact. When implemented correctly, it drastically reduces the risk of lateral movement within a compromised system and helps enforce least-privilege access at scale.
4. Securing APIs and Software Supply Chains
Today’s applications are built with a complex web of APIs and third-party libraries. While these tools speed up development, they also expand the attack surface. Securing APIs and the software supply chain is now a top priority for any modern development team.
What’s Changed:
- API posture management:Modern API gateways enforce rate limits, behavior monitoring, and token-based access.
- SBOMs (Software Bill of Materials): Now essential, SBOMs track every component used in your app for rapid vulnerability response.
- Blockchain verification: Emerging tools use blockchain to confirm the integrity of packages and third-party code sources.
By gaining visibility into what your application is built from—and how its components behave—teams can more effectively guard against zero-day vulnerabilities, dependency confusion attacks, and unauthorized data exposure. This level of supply chain awareness is a key component of application resilience.
Want to find out how much it costs to build your dream app or web app?
5. Future-Proofing with Confidential Computing & Quantum-Safe Encryption
With global data privacy laws tightening and the quantum era looming on the horizon, long-term data protection is becoming a top concern. New cryptographic models and hardware-based protections are laying the groundwork for a more secure future.
What’s Changed:
- Confidential computing: Trusted Execution Environments (TEEs) allow secure data processing in untrusted environments like public cloud.
- Post-quantum cryptography: Hybrid encryption methods are being implemented now to protect data from future quantum decryption threats.
- In-use data protection: Encryption used to be about rest and transit—now it extends to active data being computed on.
These technologies represent the cutting edge of application security, ensuring that data remains protected even during computation and against future quantum attacks. Organizations adopting these innovations today are building a more resilient, forward-compatible foundation for tomorrow.
Lizard Global: Security That’s Proactive, Continuous, and Smart
The landscape of application security has transformed—from a reactive process to an integrated, intelligent discipline that spans the entire development lifecycle. Each of these five advancements reflects a broader trend: the need for speed, precision, and resilience in the face of growing complexity and evolving threats.
, embedding these modern practices will keep your applications secure, compliant, and competitive in an increasingly hostile digital world.
At Lizard Global, we continue to evolve our security practices to match this fast-moving landscape—helping you stay secure while you innovate.
Join 2000+ subscribers
Stay in the loop with everything you need to know

5 Game-Changing Advancements in Application Security
Application security has evolved far beyond passwords and firewalls. From AI-powered threat detection to quantum-safe encryption, explore the modern strategies that top companies use to stay ahead of evolving cyber threats.
Remember the days when application security was just about strong passwords and firewalls? Seeing that today’s cyberthreats have become more complex, the ways we secure our digital products have had to evolve. The rise of microservices, APIs, remote development teams, and global regulatory standards has created a new playing field—one that demands smarter, faster, and more integrated solutions.
We’re breaking down the five transformative advancements that have fundamentally reshaped how we protect modern applications. From AI-powered threat detection to quantum-resistant encryption, these innovations are not just upgrades—they’re essential for building resilient, future-ready digital systems.
1. Shift-Left Security: Embedding Protection from the Start
Gone are the days when security was treated as a final checkpoint before release. In development cycles today, vulnerabilities introduced early can snowball into massive liabilities. That’s why modern application security starts with the code itself—a practice known as "shifting left."

What’s Changed:
- Static Application Security Testing (SAST) + Software Composition Analysis (SCA) integration: Unified tools now scan both custom and third-party code in one go, identifying full exploit chains.
- Security-as-Code: Infrastructure and policies are embedded directly into code and CI/CD pipelines, automating compliance.
- Platform Engineering-led Security: Centralized tools and security automation are now managed by platform teams for consistency at scale.
By catching and resolving vulnerabilities earlier, organizations reduce risk, save time and money, and ensure developers are actively contributing to a more secure product. This culture shift is the foundation of proactive, scalable application security.
2. AI-Driven Defense: Real-Time, Predictive Protection
As cyberattacks become more sophisticated, reactive security methods struggle to keep up. Artificial Intelligence and Machine Learning have emerged as crucial allies in defending applications, offering speed, accuracy, and predictive power that manual monitoring simply can’t match.

What’s Changed:
- Live threat detection: AI analyzes behavior in real time, identifying anomalies faster than human teams ever could.
- Predictive vulnerability management: ML models prioritize the most critical issues, reducing noise and alert fatigue.
- Self-learning firewalls: Next-gen firewalls adapt to evolving traffic patterns, offering dynamic protection with minimal manual tuning.
These tools don’t just help security teams respond—they help prevent attacks before they happen. AI is enabling a shift from reactive firefighting to proactive defense, making it a game-changer for application security teams.
3. Zero Trust Architecture: Never Trust, Always Verify
As applications migrate to the cloud
and users connect from everywhere, perimeter-based security is no longer enough. The Zero Trust model assumes that no entity—internal or external—should be automatically trusted. Every interaction must be verified, authenticated, and authorized.

What’s Changed:
- Continuous identity validation: All requests are verified at runtime—not just at login.
- Micro-segmentation: Applications and services are split into zones with strict access boundaries.
- RASP and ADR tools: Runtime Application Self-Protection and Application Detection & Response provide layered, real-time protection inside live applications.
Zero Trust not only prevents breaches from escalating, it ensures tighter controls over how users and services interact. When implemented correctly, it drastically reduces the risk of lateral movement within a compromised system and helps enforce least-privilege access at scale.
4. Securing APIs and Software Supply Chains
Today’s applications are built with a complex web of APIs and third-party libraries. While these tools speed up development, they also expand the attack surface. Securing APIs and the software supply chain is now a top priority for any modern development team.

What’s Changed:
- API posture management:Modern API gateways enforce rate limits, behavior monitoring, and token-based access.
- SBOMs (Software Bill of Materials): Now essential, SBOMs track every component used in your app for rapid vulnerability response.
- Blockchain verification: Emerging tools use blockchain to confirm the integrity of packages and third-party code sources.
By gaining visibility into what your application is built from—and how its components behave—teams can more effectively guard against zero-day vulnerabilities, dependency confusion attacks, and unauthorized data exposure. This level of supply chain awareness is a key component of application resilience.
Want to find out how much it costs to build your dream app or web app?
5. Future-Proofing with Confidential Computing & Quantum-Safe Encryption
With global data privacy laws tightening and the quantum era looming on the horizon, long-term data protection is becoming a top concern. New cryptographic models and hardware-based protections are laying the groundwork for a more secure future.

What’s Changed:
- Confidential computing: Trusted Execution Environments (TEEs) allow secure data processing in untrusted environments like public cloud.
- Post-quantum cryptography: Hybrid encryption methods are being implemented now to protect data from future quantum decryption threats.
- In-use data protection: Encryption used to be about rest and transit—now it extends to active data being computed on.
These technologies represent the cutting edge of application security, ensuring that data remains protected even during computation and against future quantum attacks. Organizations adopting these innovations today are building a more resilient, forward-compatible foundation for tomorrow.
Lizard Global: Security That’s Proactive, Continuous, and Smart
The landscape of application security has transformed—from a reactive process to an integrated, intelligent discipline that spans the entire development lifecycle. Each of these five advancements reflects a broader trend: the need for speed, precision, and resilience in the face of growing complexity and evolving threats.
, embedding these modern practices will keep your applications secure, compliant, and competitive in an increasingly hostile digital world.
At Lizard Global, we continue to evolve our security practices to match this fast-moving landscape—helping you stay secure while you innovate.
Join 2000+ subscribers
Stay in the loop with everything you need to know
FAQs

What are the most common threats to application security today?
What is Zero Trust in application security?
How does AI help in securing applications?
What is an SBOM and why is it important?
What is confidential computing?
Are companies preparing for quantum computing threats?
How can I integrate security into my app development process?
What is Runtime Application Self-Protection (RASP)?
similar reads







