Security vulnerabilities
SQL Injection (SQLi)
+ 7 more ...
7 Common Security Vulnerabilities and How to Mitigate Them

26 Sep 2024
by Chathuri, Head of Software Engineering, & Nadiy, Senior Content Writer

26 Sep 2024
by Chathuri, Head of Software Engineering, & Nadiy, Senior Content Writer
Security vulnerabilities
SQL Injection (SQLi)
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Web application security
Input validation
Secure authentication
Security misconfigurations
Mitigating security threats
7 Common Security Vulnerabilities and How to Mitigate Them
Table of contents
Contact us
We will get back to you in the next 48 hours.

Common Security Vulnerabilities and How to Mitigate Them
Cybersecurity vulnerabilities like SQL Injection, XSS, and CSRF can wreak havoc on your web applications if left unchecked. Learn about the most common security flaws and the strategies you can use to mitigate them, from input validation to strong password policies. Secure your system before attackers strike!
key takeaways
Organizations, whether large enterprises or small startups, are constantly faced with the growing complexity of cybersecurity threats. Vulnerabilities in software can be exploited to access sensitive data, disrupt services, or compromise business operations. The implications of these attacks are often catastrophic, resulting in financial loss, reputational damage, and legal repercussions.
We will delve into some of the most common security vulnerabilities—SQL Injection (SQLi), Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and others—and explore effective strategies to mitigate these risks in this blog. Understanding these threats and knowing how to defend against them is crucial for developers, security professionals, and business owners alike.
1. SQL Injection (SQLi)
SQL Injection is one of the oldest and most widespread security vulnerabilities. It occurs when attackers inject malicious SQL code into a query through user inputs, manipulating a web application’s database. This can allow unauthorized access to sensitive information such as usernames, passwords, or financial records, as well as the ability to modify or delete database entries.
How It Works:
SQL Injection exploits improperly sanitized user inputs. When a web application directly incorporates user-supplied data into SQL queries without properly validating it, the attacker can alter the query's structure.
Example:
In a vulnerable login form, an SQL query might look like this:
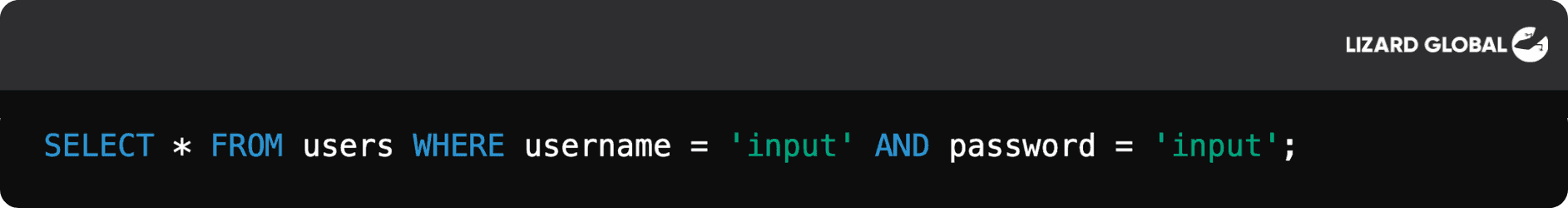
If the attacker enters ' OR '1'='1' -- as the username and password, the SQL query would become:
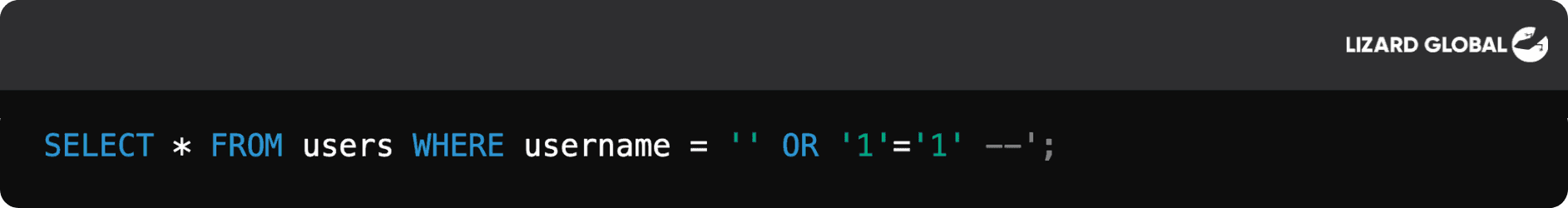
This query bypasses authentication, returning all users from the database since '1'='1' is always true.
Consequences:
- Unauthorized access to sensitive data
- Data corruption or deletion
- Full database control by the attacker
Mitigation Strategies:
- Prepared Statements and Parameterized Queries: These ensure that user inputs are treated strictly as data and not executable code. For example:
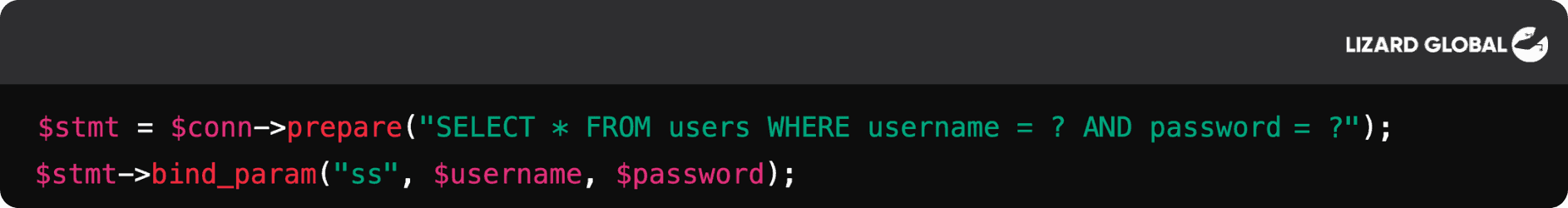
Input Validation: Restrict the types of inputs allowed by the application. For example, only permit alphanumeric characters for username fields.
Use of ORM (Object-Relational Mapping) Frameworks: These frameworks, like Hibernate or Sequelize, provide abstractions over SQL, reducing the risk of direct SQL injection by handling queries securely.
Principle of Least Privilege: Limit database permissions so that even if an attack succeeds, it only has minimal access to data.
Still not convinced on why cybersecurity matters? Improve your knowledge on it here!
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is another common and dangerous vulnerability, allowing attackers to inject malicious scripts into websites. These scripts are then executed in the browsers of unsuspecting users, potentially leading to data theft, session hijacking, or the installation of malicious software.
Types of XSS:
Stored XSS (Persistent XSS): The malicious script is stored on the server (e.g., in a database) and is delivered to other users when they access the compromised page.
Reflected XSS (Non-persistent XSS): The malicious script is reflected off a web server (via a query parameter or form submission) and executed immediately in the user’s browser.
DOM-Based XSS: This vulnerability occurs entirely on the client side, where the web page's DOM is modified based on untrusted data, leading to script execution.
Example:
An attacker could insert a malicious script into a comment field of a website, like:
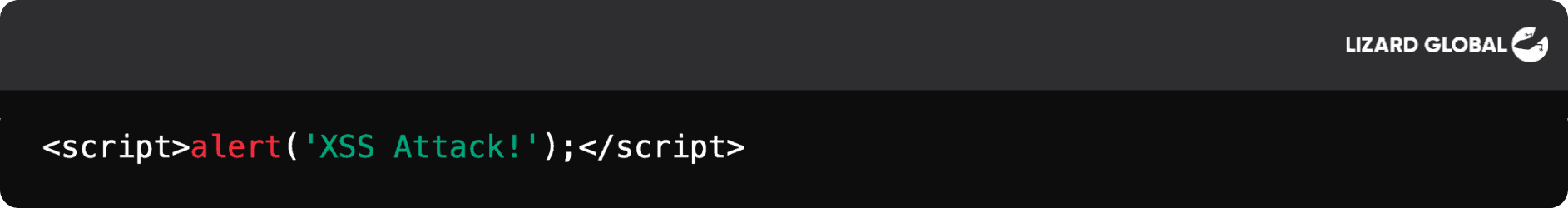
When another user views that page, the script runs in their browser, potentially giving the attacker access to sensitive information like cookies.
Mitigation Strategies:
Output Encoding: Properly encode user inputs before displaying them on the web page. For example, escape special HTML characters like " < " , " > ", and "&" to ensure that they are treated as text rather than executable code.
Example in PHP:
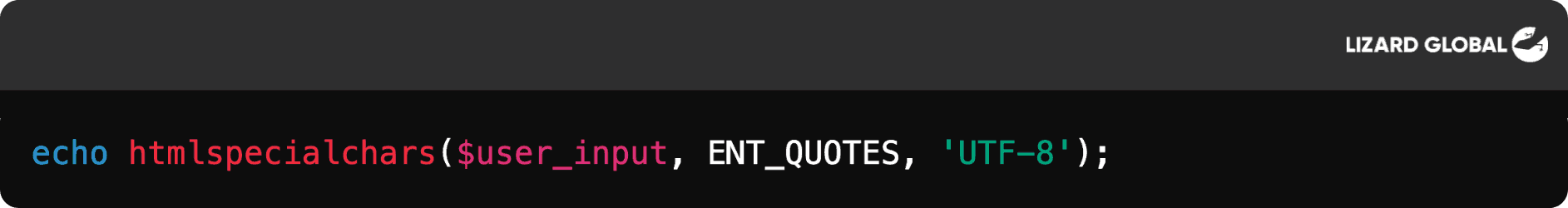
Content Security Policy (CSP): Implement a strong CSP to control what resources (scripts, styles, etc.) can run on a webpage. CSPs can prevent the execution of unauthorized scripts.
Example of a basic CSP:
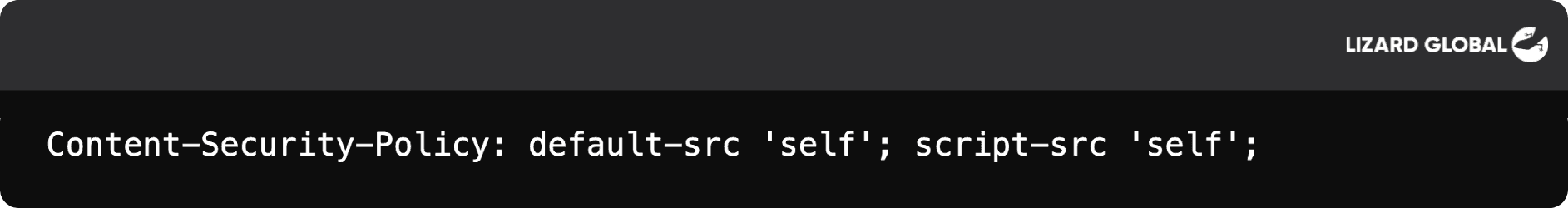
Sanitize User Inputs: Remove or neutralize dangerous characters or code from user inputs. Many libraries exist for different programming languages to sanitize inputs based on the context (e.g., HTML, JavaScript).
Proper Input Validation: Avoid allowing any untrusted user input directly into your HTML, JavaScript, or DOM.
Cybersecurity is crucial for any business and we know how to ensure your mobile app or web app are secure! Learn how Lizard Global develops your platform with security as our topmost priority!
3. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is a type of attack that tricks authenticated users into performing actions they did not intend. The attacker creates a malicious request that uses the user's credentials (e.g., cookies) to execute actions like transferring money or changing account settings without the user's consent.
How It Works:
The attacker crafts a request and tricks the user into visiting a page that sends this request. Since the user is already authenticated (with a session cookie), the server processes the malicious request as if it were legitimate.
Mitigation Strategies:
Anti-CSRF Tokens: Incorporate unique tokens in forms and requests, which the server verifies to ensure requests are legitimate. Without the correct token, the server will reject the request.
Example using Django:
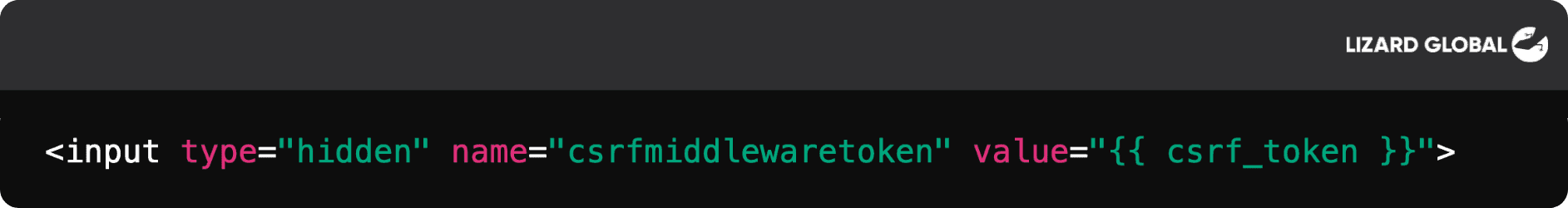
SameSite Cookie Attribute: This prevents the browser from sending cookies along with cross-site requests. Setting the
SameSite=Strictflag ensures that cookies are only sent in requests originating from your own domain.Example:
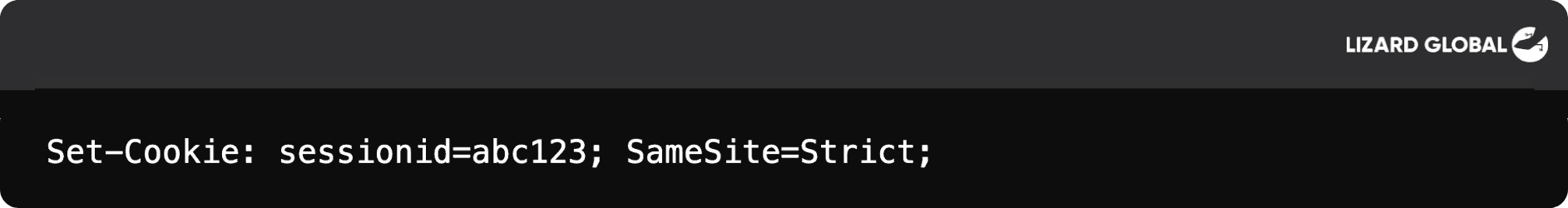
Custom Headers: Use custom headers in requests that are not typically allowed in cross-origin requests, ensuring that the request originates from a trusted source.
Double Submit Cookie Pattern: Store the CSRF token in both a cookie and a hidden form field, and compare them on the server side.
4. Broken Authentication
Broken authentication vulnerabilities are a critical issue in web security. They occur when attackers exploit flaws in the implementation of authentication mechanisms. Weak passwords, session management errors, and insecure password recovery processes can all lead to unauthorized access and identity theft.
Consequences of Broken Authentication:
- Unauthorized access to user accounts
- Credential theft
- Privilege escalation
Mitigation Strategies:
Strong Password Policies: Enforce the use of strong passwords by requiring a minimum number of characters, the use of both uppercase and lowercase letters, numbers, and symbols. Implement password complexity checks during user registration and password changes.
Multi-Factor Authentication (MFA): Require users to provide two or more verification methods, such as a password plus a one-time code sent to their phone, to ensure a higher level of security.
Session Management: Use secure session tokens, invalidate session tokens after logout, and implement session timeouts after periods of inactivity.
Secure Password Storage: Always hash passwords using a strong cryptographic hash function like bcrypt or Argon2. Never store plain text passwords.
Account Lockout: After a number of failed login attempts, temporarily lock the user’s account to prevent brute force attacks.
Do you know the importance of authentication in software development? Read on to find out what it is and why is it so important!
5. Insecure Deserialization
Insecure deserialization occurs when an application takes untrusted data and deserializes it into an object. If attackers can control the data, they can manipulate the object or even execute arbitrary code.
How It Works:
Deserialization vulnerabilities are often exploited when untrusted data is deserialized without sufficient validation. An attacker could alter serialized objects to escalate privileges or inject malicious code.
Mitigation Strategies:
Validate Untrusted Data: Ensure that any data used for deserialization is validated before use.
Implement Integrity Checks: Add checks such as cryptographic signatures to ensure that the data has not been tampered with before deserialization.
Limit Serialization: Where possible, avoid serializing sensitive data or using non-serializable data formats (like JSON) that reduce risks associated with deserialization.
Did you know there were 300 million cyberattack victims in 2023? Learn why Software Security is crucial to your business and customers.
6. Security Misconfiguration
Security misconfigurations are often the result of poor server and application setup, such as default credentials, open ports, unnecessary services, and exposed sensitive data. Attackers look for these weak points to exploit and gain unauthorized access.
Mitigation Strategies:
Secure Default Configurations: Always start with secure default settings. Disable unused services, features, or endpoints that are not necessary.
Regular Updates and Patching: Ensure that software is regularly updated with security patches to prevent the exploitation of known vulnerabilities.
Automated Security Scanning: Use automated tools to scan your application for misconfigurations and vulnerabilities regularly.
Principle of Least Privilege: Limit access to systems, services, and files only to those who need it, reducing the attack surface.
Sometimes the best decision is to seek out professional advice to ensure the best for your app security. Read on to find out what services they offer to secure your platform.
7. Insufficient Logging and Monitoring
Without sufficient logging and monitoring, cyberattacks may
go undetected for extended periods, allowing attackers to cause more damage before an organization can respond.
Mitigation Strategies:
Comprehensive Logging: Log all key events such as login attempts, access to sensitive data, and administrative actions.
Alerting Systems: Use real-time alerting systems to notify administrators of suspicious activity, such as multiple failed login attempts or access from unknown locations.
Regular Audits: Conduct regular security audits to detect any potential misconfigurations or vulnerabilities in your application.
How Lizard Global Helps Secure Your Application
Web application security is an ongoing challenge that requires constant vigilance and proactive mitigation. SQL Injection, XSS, CSRF, broken authentication, and other vulnerabilities are among the most common threats developers must contend with. By understanding how these vulnerabilities work and implementing proper mitigation strategies you can significantly reduce the risk of being compromised.

Here at Lizard Global we take an extra step in ensuring our infrastructure is secure by architecting our backend as microservices. This is where systems are composed of small, independent service modules which perform a specific function and operate independently.
For businesses looking to enhance their cybersecurity posture, reach out to us today to build a secure app with us - a trusted mobile app and web app development company that ensures your applications and data are protected from the growing number of sophisticated cyberattacks!
Join 2000+ subscribers
Stay in the loop with everything you need to know

Common Security Vulnerabilities and How to Mitigate Them
Cybersecurity vulnerabilities like SQL Injection, XSS, and CSRF can wreak havoc on your web applications if left unchecked. Learn about the most common security flaws and the strategies you can use to mitigate them, from input validation to strong password policies. Secure your system before attackers strike!
Organizations, whether large enterprises or small startups, are constantly faced with the growing complexity of cybersecurity threats. Vulnerabilities in software can be exploited to access sensitive data, disrupt services, or compromise business operations. The implications of these attacks are often catastrophic, resulting in financial loss, reputational damage, and legal repercussions.
We will delve into some of the most common security vulnerabilities—SQL Injection (SQLi), Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and others—and explore effective strategies to mitigate these risks in this blog. Understanding these threats and knowing how to defend against them is crucial for developers, security professionals, and business owners alike.
1. SQL Injection (SQLi)
SQL Injection is one of the oldest and most widespread security vulnerabilities. It occurs when attackers inject malicious SQL code into a query through user inputs, manipulating a web application’s database. This can allow unauthorized access to sensitive information such as usernames, passwords, or financial records, as well as the ability to modify or delete database entries.
How It Works:
SQL Injection exploits improperly sanitized user inputs. When a web application directly incorporates user-supplied data into SQL queries without properly validating it, the attacker can alter the query's structure.
Example:
In a vulnerable login form, an SQL query might look like this:

If the attacker enters ' OR '1'='1' -- as the username and password, the SQL query would become:

This query bypasses authentication, returning all users from the database since '1'='1' is always true.
Consequences:
- Unauthorized access to sensitive data
- Data corruption or deletion
- Full database control by the attacker
Mitigation Strategies:
- Prepared Statements and Parameterized Queries: These ensure that user inputs are treated strictly as data and not executable code. For example:

Input Validation: Restrict the types of inputs allowed by the application. For example, only permit alphanumeric characters for username fields.
Use of ORM (Object-Relational Mapping) Frameworks: These frameworks, like Hibernate or Sequelize, provide abstractions over SQL, reducing the risk of direct SQL injection by handling queries securely.
Principle of Least Privilege: Limit database permissions so that even if an attack succeeds, it only has minimal access to data.
Still not convinced on why cybersecurity matters? Improve your knowledge on it here!
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is another common and dangerous vulnerability, allowing attackers to inject malicious scripts into websites. These scripts are then executed in the browsers of unsuspecting users, potentially leading to data theft, session hijacking, or the installation of malicious software.
Types of XSS:
Stored XSS (Persistent XSS): The malicious script is stored on the server (e.g., in a database) and is delivered to other users when they access the compromised page.
Reflected XSS (Non-persistent XSS): The malicious script is reflected off a web server (via a query parameter or form submission) and executed immediately in the user’s browser.
DOM-Based XSS: This vulnerability occurs entirely on the client side, where the web page's DOM is modified based on untrusted data, leading to script execution.
Example:
An attacker could insert a malicious script into a comment field of a website, like:

When another user views that page, the script runs in their browser, potentially giving the attacker access to sensitive information like cookies.
Mitigation Strategies:
Output Encoding: Properly encode user inputs before displaying them on the web page. For example, escape special HTML characters like " < " , " > ", and "&" to ensure that they are treated as text rather than executable code.
Example in PHP:

Content Security Policy (CSP): Implement a strong CSP to control what resources (scripts, styles, etc.) can run on a webpage. CSPs can prevent the execution of unauthorized scripts.
Example of a basic CSP:

Sanitize User Inputs: Remove or neutralize dangerous characters or code from user inputs. Many libraries exist for different programming languages to sanitize inputs based on the context (e.g., HTML, JavaScript).
Proper Input Validation: Avoid allowing any untrusted user input directly into your HTML, JavaScript, or DOM.
Cybersecurity is crucial for any business and we know how to ensure your mobile app or web app are secure! Learn how Lizard Global develops your platform with security as our topmost priority!
3. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is a type of attack that tricks authenticated users into performing actions they did not intend. The attacker creates a malicious request that uses the user's credentials (e.g., cookies) to execute actions like transferring money or changing account settings without the user's consent.
How It Works:
The attacker crafts a request and tricks the user into visiting a page that sends this request. Since the user is already authenticated (with a session cookie), the server processes the malicious request as if it were legitimate.
Mitigation Strategies:
Anti-CSRF Tokens: Incorporate unique tokens in forms and requests, which the server verifies to ensure requests are legitimate. Without the correct token, the server will reject the request.
Example using Django:

SameSite Cookie Attribute: This prevents the browser from sending cookies along with cross-site requests. Setting the
SameSite=Strictflag ensures that cookies are only sent in requests originating from your own domain.Example:

Custom Headers: Use custom headers in requests that are not typically allowed in cross-origin requests, ensuring that the request originates from a trusted source.
Double Submit Cookie Pattern: Store the CSRF token in both a cookie and a hidden form field, and compare them on the server side.
4. Broken Authentication
Broken authentication vulnerabilities are a critical issue in web security. They occur when attackers exploit flaws in the implementation of authentication mechanisms. Weak passwords, session management errors, and insecure password recovery processes can all lead to unauthorized access and identity theft.
Consequences of Broken Authentication:
- Unauthorized access to user accounts
- Credential theft
- Privilege escalation
Mitigation Strategies:
Strong Password Policies: Enforce the use of strong passwords by requiring a minimum number of characters, the use of both uppercase and lowercase letters, numbers, and symbols. Implement password complexity checks during user registration and password changes.
Multi-Factor Authentication (MFA): Require users to provide two or more verification methods, such as a password plus a one-time code sent to their phone, to ensure a higher level of security.
Session Management: Use secure session tokens, invalidate session tokens after logout, and implement session timeouts after periods of inactivity.
Secure Password Storage: Always hash passwords using a strong cryptographic hash function like bcrypt or Argon2. Never store plain text passwords.
Account Lockout: After a number of failed login attempts, temporarily lock the user’s account to prevent brute force attacks.
Do you know the importance of authentication in software development? Read on to find out what it is and why is it so important!
5. Insecure Deserialization
Insecure deserialization occurs when an application takes untrusted data and deserializes it into an object. If attackers can control the data, they can manipulate the object or even execute arbitrary code.
How It Works:
Deserialization vulnerabilities are often exploited when untrusted data is deserialized without sufficient validation. An attacker could alter serialized objects to escalate privileges or inject malicious code.
Mitigation Strategies:
Validate Untrusted Data: Ensure that any data used for deserialization is validated before use.
Implement Integrity Checks: Add checks such as cryptographic signatures to ensure that the data has not been tampered with before deserialization.
Limit Serialization: Where possible, avoid serializing sensitive data or using non-serializable data formats (like JSON) that reduce risks associated with deserialization.
Did you know there were 300 million cyberattack victims in 2023? Learn why Software Security is crucial to your business and customers.
6. Security Misconfiguration
Security misconfigurations are often the result of poor server and application setup, such as default credentials, open ports, unnecessary services, and exposed sensitive data. Attackers look for these weak points to exploit and gain unauthorized access.
Mitigation Strategies:
Secure Default Configurations: Always start with secure default settings. Disable unused services, features, or endpoints that are not necessary.
Regular Updates and Patching: Ensure that software is regularly updated with security patches to prevent the exploitation of known vulnerabilities.
Automated Security Scanning: Use automated tools to scan your application for misconfigurations and vulnerabilities regularly.
Principle of Least Privilege: Limit access to systems, services, and files only to those who need it, reducing the attack surface.
Sometimes the best decision is to seek out professional advice to ensure the best for your app security. Read on to find out what services they offer to secure your platform.
7. Insufficient Logging and Monitoring
Without sufficient logging and monitoring, cyberattacks may
go undetected for extended periods, allowing attackers to cause more damage before an organization can respond.
Mitigation Strategies:
Comprehensive Logging: Log all key events such as login attempts, access to sensitive data, and administrative actions.
Alerting Systems: Use real-time alerting systems to notify administrators of suspicious activity, such as multiple failed login attempts or access from unknown locations.
Regular Audits: Conduct regular security audits to detect any potential misconfigurations or vulnerabilities in your application.
How Lizard Global Helps Secure Your Application
Web application security is an ongoing challenge that requires constant vigilance and proactive mitigation. SQL Injection, XSS, CSRF, broken authentication, and other vulnerabilities are among the most common threats developers must contend with. By understanding how these vulnerabilities work and implementing proper mitigation strategies you can significantly reduce the risk of being compromised.

Here at Lizard Global we take an extra step in ensuring our infrastructure is secure by architecting our backend as microservices. This is where systems are composed of small, independent service modules which perform a specific function and operate independently.
For businesses looking to enhance their cybersecurity posture, reach out to us today to build a secure app with us - a trusted mobile app and web app development company that ensures your applications and data are protected from the growing number of sophisticated cyberattacks!
Join 2000+ subscribers
Stay in the loop with everything you need to know
FAQs

What is SQL Injection?
How can I prevent Cross-Site Scripting (XSS)?
What is Cross-Site Request Forgery (CSRF)?
What are anti-CSRF tokens?
Why is security configuration important?





